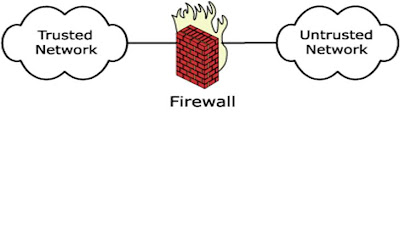
Network Firewall
A Network Firewall is a system or group of systems used to control access between two networks – a trusted and an untrusted network
A firewall is considered a first line of defense in protecting private information.
Need of firewall:
If a user spend a lot of time on the internet and is not behind a firewall then the system can be easily attacked. Therefore, protection between user and the internet is probably the most important thing that one needs to have (after getting virus checking software and performing regular backups).
For those with a DSL, cable modem or other "always-on" connection, user must get a firewall. This is critical, as machine is always live and it most likely has a fixed IP address. This makes it easier for system to be "found" and attacked.
Unprotected system using a DSL modem:
As we can see, someone on the internet can attack the computer system easily as the DSL modem provides no protection (some DSL modems have built-in firewalls). An attacker can get through any type of modem - DSL, cable, 56K, 28.8 or whatever.
Protected system using a DSL modem:
Firewall protection system:
All messages entering or leaving the intranet pass through the firewall, which examines each message and blocks whether it meets the specified security criteria. If it does, it is routed between the networks, otherwise it is stopped. A firewall filters both inbound and outbound traffic. It can also manage public access to private networked resources such as host applications. It can be used to log all attempts to enter the private network and trigger alarms when hostile or unauthorized entry is attempted.
Types of Firewalls:
1. Software Firewall
2. Hardware Firewall
2. Hardware Firewall
1.Software Firewall:
A software firewall runs on our computer system in the background. It intercepts each network request and determines if the request is valid or not. This type of firewall is a software package installed on a server operating system which turns the server into a full fledged firewall.
Advantages & Disadvantages of Software firewalls:
Advantages:
1. They are generally very inexpensive.
2. They are very easy to configure.
Disadvantages:
1. Since they run on computer they require resources (CPU, memory and disk space) from system.
2. They can introduce incompatibilities into operating system.
3. Users must install exactly the correct version for their operating system.
Hardware Firewall:
A hardware firewall is generally a small box which sits between computer and modem.
These firewalls are designed to handle large amounts of network traffic. Hardware firewalls are often placed on the perimeter of the network to filter the internet noise and only allow pre-determined traffic into the network. Sometimes hardware firewalls are used in conjunction with software firewalls so the hardware firewall filters out the traffic and the software firewall inspects the network traffic.
Advantages:
1. They tend to provide more complete protection than software firewalls
2. A hardware firewall can protect more than one system at a time
3. They do not affect system performance since they do not run on system.
4. They are independent of operating system and applications.
Disadvantages:
1. They tend to be expensive, although if we have a number of machines to protect it can cost less to purchase one hardware firewall than a number of copies of a software product.
2. Since they do not run on our computer, they can be challenging to configure.
Techniques of firewalls
There are several types of firewall techniques:
1. Packet filter: Looks at each packet entering or leaving the network and accepts or rejects it based on user-defined rules. Packet filtering is fairly effective and transparent to users, but it is difficult to configure. In addition, it is susceptible to IP spoofing.
2. Application gateway: Applies security mechanisms to specific applications, such as FTP and Telnet servers. This is very effective, but can impose performance degradation.
3. Circuit-level gateway: Applies security mechanisms when a TCP or UDP connection is established. Once the connection has been made, packets can flow between the hosts without further checking.
4.Proxy server: Intercepts all messages entering and Leaving the network. The proxy server effectively hides the true network addresses.
Each method uses information from different layers of the Open Systems Interconnection (OSI) model. These methods are based on how firewalls use both pre-configured rules and filters and information gathered from packets and sessions to determine whether to allow or deny traffic.
5. Packet Filtering
Packet filtering is the simplest packet screening method. A packet filtering firewall does exactly what its name implies -- it filters packets. The most common implementation is on a router or dual-homed gateway.
The packet filtering process is accomplished in the following manner
As each packet passes through the firewall, it is examined and information contained in the header is compared to a pre-configured set of rules or filters. An allow or deny decision is made based on the results of the comparison.
Application Gateways/Proxies
An application gateway/proxy is considered by to be the most complex packet screening method. This type of firewall is usually implemented on a secure host system configured with two network interfaces. The application gateway/proxy acts as an intermediary between the two endpoints.
An application gateway/proxy firewall operates in the following manner :
When a client issues a request from the untrusted network, a connection is established with the application gateway/proxy. The proxy determines if the request is valid (by comparing it to any rules or filters) and then sends a new request on behalf of the client to the destination. By using this method, a direct connection is never made from the trusted network to the untrusted network and the request appears to have originated from the application gateway/proxy.
The request is answered in the same manner. The response is sent back to the application gateway/proxy, which determines if it is valid and then sends it on to the client. By breaking the client/server model, this type of firewall can effectively hide the trusted network from the untrusted network. The application gateway/proxy actually builds a new request, only copying known acceptable commands before sending it on to the destination.
This is considered a highly secure method of firewall protection, application gateways require great memory and processor resources compared to other firewall technologies, such as stateful inspection.
Stateful Packet Inspection
Stateful packet inspection uses the same fundamental packet screening technique that packet filtering does. In addition, it examines the packet header information from the network layer of the OSI model to the application layer to verify that the packet is part of a legitimate connection and the protocols are behaving as expected.
The stateful packet inspection process is accomplished in the following manner. As packets pass through the firewall, packet header information is examined and fed into a dynamic state table where it is stored. The packets are compared to pre-configured rules or filters and allow or deny decisions are made based on the results of the comparison. The data in the state table is then used to evaluate subsequent packets to verify that they are part of the same connection.
Circuit-level Gateway
Unlike a packet filtering firewall, a circuit-level gateway does not examine individual packets. Instead, circuit-level gateways monitor TCP or UDP sessions. Once a session has been established, it leaves the port open to allow all other packets belonging to that session to pass. The port is closed when the session is terminated.
In many respects this method of packet screening resembles application gateways/proxies, but circuit-level gateways operate at the transport layer (layer 4) of the OSI model.









Comments